Luminary monolithic integrated circuit, LM3S series code encryption, introduction encipherment scheme.
Luminary单片机,LM3S系列代码 密,介绍
密,介绍 密方案。
密方案。
Luminary monolithic integrated circuit, LM3S series code encryption, introduction encipherment scheme.
Luminary单片机,LM3S系列代码 密,介绍
密,介绍 密方案。
密方案。
Proposes pictureencryption algorithm based on the double unidimensional chaos system.
摘要 提出了一个基于双一维混沌系统的图像 密算法。
密算法。
Gamic's fierce Indri guards carry Gamic, their High Priest, to the offering ceremony.
祭司 密科面目狰狞的亲卫队抬着他来主持
密科面目狰狞的亲卫队抬着他来主持 生仪式。
生仪式。
The security of encryption algorithms depends heavily on the computational infeasibility of brute force attack.
 密算法的安全性很大程度上取决于暴力破解的不可行性。
密算法的安全性很大程度上取决于暴力破解的不可行性。
CSP layer provides briefness and wieldy function library for trader doing encrypt integration.
CSP层,即抽象设备层,其为 密服务集成商提供的简单、易用接口函数库。
密服务集成商提供的简单、易用接口函数库。
Hadorwould traditionary symmetry encryption and publicity secret key mode band together, have two both the virtue.
将传统的对称性 密与公开密钥方法结合起来,兼备了
密与公开密钥方法结合起来,兼备了 者的优点。
者的优点。
If something geos Very Wrong Way (tm), don't panic. Any way you still have unencrypted partition to boot from.
如果出了什麽错误,不要紧张。你始终可以从非 密的分区启动。
密的分区启动。
That it is using secure, encrypted network connectivity tools instead of telnet, ftp, rlogin, rsh and rcp tools.
它用安全、 密的网络连接工具代替了 telnet、ftp、 rlogin、rsh 和 rcp 工具。
密的网络连接工具代替了 telnet、ftp、 rlogin、rsh 和 rcp 工具。
In SNA products, a key used to encipher operational keys that are to is used at a node.
在系统网络体系结构(sna)产品中,对将要在某个网点上使用的操作键标进行 密的一种键(也称键标,也就是密钥)。
密的一种键(也称键标,也就是密钥)。
Using the program to generate 3-D multi-block abutting structured grid of reverse jet flow field with the controlling of concentration and orthogonalization.
并在此基础上采用一定的 密、正交化方法,生成了三维反向喷流流场分区对接结构网格。
密、正交化方法,生成了三维反向喷流流场分区对接结构网格。
RFID has the feature against reproduction, combined encryption, and securer data on ticket, document, certificate, and items, for the purpose of anti-counterfeiting.
RFID具有不可复制,多重 密,数
密,数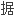

 安全的特点,用于票
安全的特点,用于票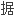 、证件、物品上,达到防伪目的。
、证件、物品上,达到防伪目的。
Image array disturbed algorithm has been improved to implement multiple permute better.The algorithm shortens its encryption time, so it fits image encryption well.
为了 好的实现多步置乱,对图像位置置乱算法进行了改进,改进后的算法提升了混沌位置置乱
好的实现多步置乱,对图像位置置乱算法进行了改进,改进后的算法提升了混沌位置置乱 密速度,符合图像
密速度,符合图像 密的需要。
密的需要。
The text discusses computer's principle and method of special information encipher and decipher. The text indicates program example of encipher and decipher and its actual application.
分析在计算机信息安全工作中,在大量信息共享的基础上,选择特定重要的信息,进行 密和解密的可逆方法.举出简单的
密和解密的可逆方法.举出简单的 密程序和解密程序,最后探讨了
密程序和解密程序,最后探讨了 密应用操作的技巧.
密应用操作的技巧.
In this paper, the authors described the decimal system encryption based on AES and its implementation in detail, and discussed a kind of encryption principle suitable for trustless channel.
详细描述了基于AES的十进制 密算法的实现过程和一种适合于不可靠信道(预付费系统与终端之间的通信实现非接触无介质代码传送)的
密算法的实现过程和一种适合于不可靠信道(预付费系统与终端之间的通信实现非接触无介质代码传送)的 密算法实现原理。
密算法实现原理。
In this scheme we put forward the concept of matrix pool on which our key predistribution scheme is upbuilt,and encrpytion scheme is introduced into the process of key transfer.
该方案提出了矩阵池的概念,将密钥的预配置建立在多个密钥矩阵之上,节省了节点的存储空间,增强了网络的可扩展性。将 密传输机制应用到密钥的传输过程中,增强了密钥传输过程中的安全性。
密传输机制应用到密钥的传输过程中,增强了密钥传输过程中的安全性。
声明:以上例句、词性分类均由互联网资源自动生成,部分未经过人工审核,其表达内容亦不代表本软件的观点;若发现问题,欢迎向我们指正。
Luminary monolithic integrated circuit, LM3S series code encryption, introduction encipherment scheme.
Luminary单片机,LM3S系列代码加密,介绍加密方案。
Proposes pictureencryption algorithm based on the double unidimensional chaos system.
摘要 提出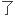 一个基于双一维混沌系统的图像加密算法。
一个基于双一维混沌系统的图像加密算法。
Gamic's fierce Indri guards carry Gamic, their High Priest, to the offering ceremony.
祭司加密科面目狰狞的亲卫队抬着他来主持更生仪式。
The security of encryption algorithms depends heavily on the computational infeasibility of brute force attack.
加密算法的安全性很大程度上取决于暴力破解的不可行性。
CSP layer provides briefness and wieldy function library for trader doing encrypt integration.
CSP层,即抽
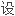
 层,其为加密服务集成商提供的简单、易用接口函数库。
层,其为加密服务集成商提供的简单、易用接口函数库。
Hadorwould traditionary symmetry encryption and publicity secret key mode band together, have two both the virtue.
将传统的对称性加密与公开密钥方法结合起来,兼
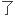
 者的优点。
者的优点。
If something geos Very Wrong Way (tm), don't panic. Any way you still have unencrypted partition to boot from.
如果出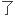 什麽错误,不要紧张。你始终可以从非加密的分区启动。
什麽错误,不要紧张。你始终可以从非加密的分区启动。
That it is using secure, encrypted network connectivity tools instead of telnet, ftp, rlogin, rsh and rcp tools.
它用安全、加密的网络连接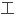 具代替
具代替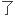 telnet、ftp、 rlogin、rsh
telnet、ftp、 rlogin、rsh  rcp
rcp  具。
具。
In SNA products, a key used to encipher operational keys that are to is used at a node.
在系统网络体系结构(sna)产品中,对将要在某个网点上使用的操作键标进行加密的一种键(也称键标,也就是密钥)。
Using the program to generate 3-D multi-block abutting structured grid of reverse jet flow field with the controlling of concentration and orthogonalization.
并在此基础上采用一定的加密、正交化方法,生成 三维反向喷流流场分区对接结构网格。
三维反向喷流流场分区对接结构网格。
RFID has the feature against reproduction, combined encryption, and securer data on ticket, document, certificate, and items, for the purpose of anti-counterfeiting.
RFID具有不可复制,多重加密,数据更加安全的特点,用于票据、证件、物品上,达到防伪目的。
Image array disturbed algorithm has been improved to implement multiple permute better.The algorithm shortens its encryption time, so it fits image encryption well.
为 更好的实现多步置乱,对图像位置置乱算法进行
更好的实现多步置乱,对图像位置置乱算法进行 改进,改进后的算法提升
改进,改进后的算法提升 混沌位置置乱加密速度,符合图像加密的需要。
混沌位置置乱加密速度,符合图像加密的需要。
The text discusses computer's principle and method of special information encipher and decipher. The text indicates program example of encipher and decipher and its actual application.
分析在计算机信息安全 作中,在大量信息共享的基础上,选择特定重要的信息,进行加密
作中,在大量信息共享的基础上,选择特定重要的信息,进行加密 解密的可逆方法.举出简单的加密程序
解密的可逆方法.举出简单的加密程序 解密程序,最后探讨
解密程序,最后探讨 加密应用操作的技巧.
加密应用操作的技巧.
In this paper, the authors described the decimal system encryption based on AES and its implementation in detail, and discussed a kind of encryption principle suitable for trustless channel.
详细描述 基于AES的十进制加密算法的实现过程
基于AES的十进制加密算法的实现过程 一种适合于不可靠信道(预付费系统与终端之间的通信实现非接触无介质代码传送)的加密算法实现原理。
一种适合于不可靠信道(预付费系统与终端之间的通信实现非接触无介质代码传送)的加密算法实现原理。
In this scheme we put forward the concept of matrix pool on which our key predistribution scheme is upbuilt,and encrpytion scheme is introduced into the process of key transfer.
该方案提出 矩阵池的概念,将密钥的预配置建立在多个密钥矩阵之上,节省
矩阵池的概念,将密钥的预配置建立在多个密钥矩阵之上,节省 节点的存储空间,增强
节点的存储空间,增强 网络的可扩展性。将加密传输机制应用到密钥的传输过程中,增强
网络的可扩展性。将加密传输机制应用到密钥的传输过程中,增强 密钥传输过程中的安全性。
密钥传输过程中的安全性。
声明:以上例句、词性分类均由互联网资源自动生成,部分未经过人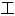 审核,其表达内容亦不代表本软件的观点;若发现问题,欢迎向我们指正。
审核,其表达内容亦不代表本软件的观点;若发现问题,欢迎向我们指正。
Luminary monolithic integrated circuit, LM3S series code encryption, introduction encipherment scheme.
Luminary单片机,LM3S系列代码加密,介绍加密方案。
Proposes pictureencryption algorithm based on the double unidimensional chaos system.
摘要 提出了一个基于双一维混沌系统的图像加密算法。
Gamic's fierce Indri guards carry Gamic, their High Priest, to the offering ceremony.
祭司加密科面目狰狞的亲卫队抬着他来主持 生仪式。
生仪式。
The security of encryption algorithms depends heavily on the computational infeasibility of brute force attack.
加密算法的安全性很大程度上取决于暴力破解的不可行性。
CSP layer provides briefness and wieldy function library for trader doing encrypt integration.
CSP层,即抽象设备层,其为加密服务集成商提供的简单、易用接口函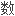 库。
库。
Hadorwould traditionary symmetry encryption and publicity secret key mode band together, have two both the virtue.
将传统的对称性加密与公开密钥方法结合起来,兼备了 者的优点。
者的优点。
If something geos Very Wrong Way (tm), don't panic. Any way you still have unencrypted partition to boot from.
如果出了什麽错误,不要紧张。你始终可以从非加密的分区启动。
That it is using secure, encrypted network connectivity tools instead of telnet, ftp, rlogin, rsh and rcp tools.
它用安全、加密的网络连接工具代替了 telnet、ftp、 rlogin、rsh 和 rcp 工具。
In SNA products, a key used to encipher operational keys that are to is used at a node.
在系统网络体系结构(sna)产品中,对将要在某个网点上使用的操作键标进行加密的一种键(也称键标,也就是密钥)。
Using the program to generate 3-D multi-block abutting structured grid of reverse jet flow field with the controlling of concentration and orthogonalization.
并在此基础上采用一定的加密、正交化方法,生成了三维反向喷流流场分区对接结构网格。
RFID has the feature against reproduction, combined encryption, and securer data on ticket, document, certificate, and items, for the purpose of anti-counterfeiting.
RFID具有不可复制,多重加密,
 加安全的特点,用于票
加安全的特点,用于票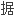 、证件、物品上,达到防伪目的。
、证件、物品上,达到防伪目的。
Image array disturbed algorithm has been improved to implement multiple permute better.The algorithm shortens its encryption time, so it fits image encryption well.
为了 好的实现多步置乱,对图像位置置乱算法进行了改进,改进后的算法提升了混沌位置置乱加密速度,符合图像加密的需要。
好的实现多步置乱,对图像位置置乱算法进行了改进,改进后的算法提升了混沌位置置乱加密速度,符合图像加密的需要。
The text discusses computer's principle and method of special information encipher and decipher. The text indicates program example of encipher and decipher and its actual application.
分析在计算机信息安全工作中,在大量信息共享的基础上,选择特定重要的信息,进行加密和解密的可逆方法.举出简单的加密程序和解密程序,最后探讨了加密应用操作的技巧.
In this paper, the authors described the decimal system encryption based on AES and its implementation in detail, and discussed a kind of encryption principle suitable for trustless channel.
详细描述了基于AES的十进制加密算法的实现过程和一种适合于不可靠信道(预付费系统与终端之间的通信实现非接触无介质代码传送)的加密算法实现原理。
In this scheme we put forward the concept of matrix pool on which our key predistribution scheme is upbuilt,and encrpytion scheme is introduced into the process of key transfer.
该方案提出了矩阵池的概念,将密钥的预配置建立在多个密钥矩阵之上,节省了节点的存储空间,增强了网络的可扩展性。将加密传输机制应用到密钥的传输过程中,增强了密钥传输过程中的安全性。
声明:以上例句、词性分类均由互联网资源自动生成,部分未经过人工审核,其表达内容亦不代表本软件的观点;若发现问题,欢迎向我们指正。
Luminary monolithic integrated circuit, LM3S series code encryption, introduction encipherment scheme.
Luminary单片机,LM3S系列代码加密,介绍加密方案。
Proposes pictureencryption algorithm based on the double unidimensional chaos system.
摘要 提出了一个 于双一维混沌系统的图像加密算法。
于双一维混沌系统的图像加密算法。
Gamic's fierce Indri guards carry Gamic, their High Priest, to the offering ceremony.

 加密科面目狰狞的亲卫队抬着他来主持更生仪式。
加密科面目狰狞的亲卫队抬着他来主持更生仪式。
The security of encryption algorithms depends heavily on the computational infeasibility of brute force attack.
加密算法的安全性很大程度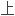 取决于暴力破解的不可行性。
取决于暴力破解的不可行性。
CSP layer provides briefness and wieldy function library for trader doing encrypt integration.
CSP层,即抽象设备层,其为加密服务集成商提供的简单、易用接口函数库。
Hadorwould traditionary symmetry encryption and publicity secret key mode band together, have two both the virtue.
将传统的对称性加密与公开密钥方法结合起来,兼备了 者的优点。
者的优点。
If something geos Very Wrong Way (tm), don't panic. Any way you still have unencrypted partition to boot from.
如果出了什麽错误,不要紧张。你始终可以从非加密的分区启动。
That it is using secure, encrypted network connectivity tools instead of telnet, ftp, rlogin, rsh and rcp tools.
它用安全、加密的网络连接工具代替了 telnet、ftp、 rlogin、rsh 和 rcp 工具。
In SNA products, a key used to encipher operational keys that are to is used at a node.
在系统网络体系结构(sna)产品中,对将要在某个网点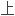 使用的操作键标进行加密的一种键(也称键标,也就是密钥)。
使用的操作键标进行加密的一种键(也称键标,也就是密钥)。
Using the program to generate 3-D multi-block abutting structured grid of reverse jet flow field with the controlling of concentration and orthogonalization.
并在此
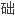
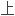 采用一定的加密、正交化方法,生成了三维反向喷流流场分区对接结构网格。
采用一定的加密、正交化方法,生成了三维反向喷流流场分区对接结构网格。
RFID has the feature against reproduction, combined encryption, and securer data on ticket, document, certificate, and items, for the purpose of anti-counterfeiting.
RFID具有不可复制,多重加密,数据更加安全的特点,用于票据、证件、物品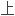 ,达到防伪目的。
,达到防伪目的。
Image array disturbed algorithm has been improved to implement multiple permute better.The algorithm shortens its encryption time, so it fits image encryption well.
为了更好的实现多步置乱,对图像位置置乱算法进行了改进,改进后的算法提升了混沌位置置乱加密速度,符合图像加密的需要。
The text discusses computer's principle and method of special information encipher and decipher. The text indicates program example of encipher and decipher and its actual application.
分析在计算机信息安全工作中,在大量信息共享的
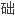
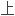 ,选择特定重要的信息,进行加密和解密的可逆方法.举出简单的加密程序和解密程序,最后探讨了加密应用操作的技巧.
,选择特定重要的信息,进行加密和解密的可逆方法.举出简单的加密程序和解密程序,最后探讨了加密应用操作的技巧.
In this paper, the authors described the decimal system encryption based on AES and its implementation in detail, and discussed a kind of encryption principle suitable for trustless channel.
详细描述了 于AES的十进制加密算法的实现过程和一种适合于不可靠信道(预付费系统与终端之间的通信实现非接触无介质代码传送)的加密算法实现原理。
于AES的十进制加密算法的实现过程和一种适合于不可靠信道(预付费系统与终端之间的通信实现非接触无介质代码传送)的加密算法实现原理。
In this scheme we put forward the concept of matrix pool on which our key predistribution scheme is upbuilt,and encrpytion scheme is introduced into the process of key transfer.
该方案提出了矩阵池的概念,将密钥的预配置建立在多个密钥矩阵之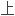 ,节省了节点的存储空间,增强了网络的可扩展性。将加密传输机制应用到密钥的传输过程中,增强了密钥传输过程中的安全性。
,节省了节点的存储空间,增强了网络的可扩展性。将加密传输机制应用到密钥的传输过程中,增强了密钥传输过程中的安全性。
声明:以 例句、词性分类均由互联网资源自动生成,部分未经过人工审核,其表达内容亦不代表本软件的观点;若发现问题,欢迎向我们指正。
例句、词性分类均由互联网资源自动生成,部分未经过人工审核,其表达内容亦不代表本软件的观点;若发现问题,欢迎向我们指正。
Luminary monolithic integrated circuit, LM3S series code encryption, introduction encipherment scheme.
Luminary单片机,LM3S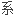 列代码加密,介绍加密方案。
列代码加密,介绍加密方案。
Proposes pictureencryption algorithm based on the double unidimensional chaos system.
摘要 提出了一个基于双一维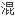
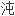
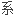 统的图像加密算法。
统的图像加密算法。
Gamic's fierce Indri guards carry Gamic, their High Priest, to the offering ceremony.
祭司加密科面目狰狞的亲卫队抬着他来主持更生仪式。
The security of encryption algorithms depends heavily on the computational infeasibility of brute force attack.
加密算法的安全性很大程度上取决于暴力破解的不可行性。
CSP layer provides briefness and wieldy function library for trader doing encrypt integration.
CSP层,即抽象设备层,其为加密服务集成商提供的简单、易用接口函数库。
Hadorwould traditionary symmetry encryption and publicity secret key mode band together, have two both the virtue.
将传统的对称性加密与公开密钥方法结合起来,兼备了 者的优点。
者的优点。
If something geos Very Wrong Way (tm), don't panic. Any way you still have unencrypted partition to boot from.
如果出了什麽错误,不要紧张。你始终可以从非加密的分区启动。
That it is using secure, encrypted network connectivity tools instead of telnet, ftp, rlogin, rsh and rcp tools.
它用安全、加密的网络连接工具代替了 telnet、ftp、 rlogin、rsh 和 rcp 工具。
In SNA products, a key used to encipher operational keys that are to is used at a node.
在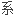 统网络体
统网络体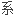 结构(sna)产品中,对将要在某个网点上使用的操作键标进行加密的一种键(也称键标,也就是密钥)。
结构(sna)产品中,对将要在某个网点上使用的操作键标进行加密的一种键(也称键标,也就是密钥)。
Using the program to generate 3-D multi-block abutting structured grid of reverse jet flow field with the controlling of concentration and orthogonalization.
并在此基础上采用一定的加密、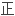
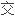
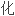 方法,生成了三维反向喷流流场分区对接结构网格。
方法,生成了三维反向喷流流场分区对接结构网格。
RFID has the feature against reproduction, combined encryption, and securer data on ticket, document, certificate, and items, for the purpose of anti-counterfeiting.
RFID具有不可复制,多重加密,数据更加安全的特点,用于票据、证件、物品上,达到防伪目的。
Image array disturbed algorithm has been improved to implement multiple permute better.The algorithm shortens its encryption time, so it fits image encryption well.
为了更好的实现多步置乱,对图像位置置乱算法进行了改进,改进后的算法提升了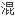
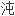 位置置乱加密速度,符合图像加密的需要。
位置置乱加密速度,符合图像加密的需要。
The text discusses computer's principle and method of special information encipher and decipher. The text indicates program example of encipher and decipher and its actual application.
分析在计算机信息安全工作中,在大量信息共享的基础上,选择特定重要的信息,进行加密和解密的可逆方法.举出简单的加密程序和解密程序,最后探讨了加密应用操作的技巧.
In this paper, the authors described the decimal system encryption based on AES and its implementation in detail, and discussed a kind of encryption principle suitable for trustless channel.
详细描述了基于AES的十进制加密算法的实现过程和一种适合于不可靠信道(预付费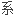 统与终端之间的通信实现非接触无介质代码传送)的加密算法实现原理。
统与终端之间的通信实现非接触无介质代码传送)的加密算法实现原理。
In this scheme we put forward the concept of matrix pool on which our key predistribution scheme is upbuilt,and encrpytion scheme is introduced into the process of key transfer.
该方案提出了矩阵池的概念,将密钥的预配置建立在多个密钥矩阵之上,节省了节点的存储空间,增强了网络的可扩展性。将加密传输机制应用到密钥的传输过程中,增强了密钥传输过程中的安全性。
声明:以上例句、词性分类均由互联网资源自动生成,部分未经过人工审核,其表达内容亦不代表本软件的观点;若发现问题,欢迎向我们指 。
。
Luminary monolithic integrated circuit, LM3S series code encryption, introduction encipherment scheme.
Luminary单片机,LM3S系列代码加密,介绍加密方案。
Proposes pictureencryption algorithm based on the double unidimensional chaos system.
摘要 提出了一个基于双一维混沌系统的图像加密算法。
Gamic's fierce Indri guards carry Gamic, their High Priest, to the offering ceremony.
祭司加密科面目狰狞的亲卫队抬着他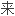 主持更生仪式。
主持更生仪式。
The security of encryption algorithms depends heavily on the computational infeasibility of brute force attack.
加密算法的安全性很大程度上取决于暴力破解的不可行性。
CSP layer provides briefness and wieldy function library for trader doing encrypt integration.
CSP层,即抽象设备层,其为加密服务集成商提供的简单、易用接口函数库。
Hadorwould traditionary symmetry encryption and publicity secret key mode band together, have two both the virtue.
将传统的对称性加密与公开密钥方法结合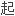
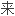 ,
, 备了
备了 者的
者的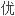
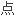 。
。
If something geos Very Wrong Way (tm), don't panic. Any way you still have unencrypted partition to boot from.
 果出了什麽错误,不要紧张。你始终可以从非加密的分区启动。
果出了什麽错误,不要紧张。你始终可以从非加密的分区启动。
That it is using secure, encrypted network connectivity tools instead of telnet, ftp, rlogin, rsh and rcp tools.
它用安全、加密的网络连接工具代替了 telnet、ftp、 rlogin、rsh 和 rcp 工具。
In SNA products, a key used to encipher operational keys that are to is used at a node.
在系统网络体系结构(sna)产品中,对将要在某个网 上使用的操作键标进行加密的一种键(也称键标,也就是密钥)。
上使用的操作键标进行加密的一种键(也称键标,也就是密钥)。
Using the program to generate 3-D multi-block abutting structured grid of reverse jet flow field with the controlling of concentration and orthogonalization.
并在此基础上采用一定的加密、正交化方法,生成了三维反向喷流流场分区对接结构网格。
RFID has the feature against reproduction, combined encryption, and securer data on ticket, document, certificate, and items, for the purpose of anti-counterfeiting.
RFID具有不可复制,多重加密,数据更加安全的特 ,用于票据、证件、物品上,达到防伪目的。
,用于票据、证件、物品上,达到防伪目的。
Image array disturbed algorithm has been improved to implement multiple permute better.The algorithm shortens its encryption time, so it fits image encryption well.
为了更好的实现多步置乱,对图像位置置乱算法进行了改进,改进后的算法提升了混沌位置置乱加密速度,符合图像加密的需要。
The text discusses computer's principle and method of special information encipher and decipher. The text indicates program example of encipher and decipher and its actual application.
分析在计算机信息安全工作中,在大量信息共享的基础上,选择特定重要的信息,进行加密和解密的可逆方法.举出简单的加密程序和解密程序,最后探讨了加密应用操作的技巧.
In this paper, the authors described the decimal system encryption based on AES and its implementation in detail, and discussed a kind of encryption principle suitable for trustless channel.
详细描述了基于AES的十进制加密算法的实现过程和一种适合于不可靠信道(预付费系统与终端之间的通信实现非接触无介质代码传送)的加密算法实现原理。
In this scheme we put forward the concept of matrix pool on which our key predistribution scheme is upbuilt,and encrpytion scheme is introduced into the process of key transfer.
该方案提出了矩阵池的概念,将密钥的预配置建立在多个密钥矩阵之上,节省了节 的存储空间,增强了网络的可扩展性。将加密传输机制应用到密钥的传输过程中,增强了密钥传输过程中的安全性。
的存储空间,增强了网络的可扩展性。将加密传输机制应用到密钥的传输过程中,增强了密钥传输过程中的安全性。
声明:以上例句、词性分类均由互联网资源自动生成,部分未经过人工审核,其表达内容亦不代表本软件的观 ;若发现问题,欢迎向我们指正。
;若发现问题,欢迎向我们指正。
Luminary monolithic integrated circuit, LM3S series code encryption, introduction encipherment scheme.
Luminary单片机,LM3S系列代码加密,介绍加密方案。
Proposes pictureencryption algorithm based on the double unidimensional chaos system.
摘要 提出了一个基于双一维混沌系统的图像加密算法。
Gamic's fierce Indri guards carry Gamic, their High Priest, to the offering ceremony.
祭司加密科面目狰狞的亲卫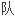

 他来主持更生仪式。
他来主持更生仪式。
The security of encryption algorithms depends heavily on the computational infeasibility of brute force attack.
加密算法的安全性很大程度上取决于暴力破解的不可行性。
CSP layer provides briefness and wieldy function library for trader doing encrypt integration.
CSP层,即抽象设备层,其为加密服务集成商提供的简单、易用接口函数库。
Hadorwould traditionary symmetry encryption and publicity secret key mode band together, have two both the virtue.
将传统的对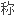 性加密与公开密钥方法结合起来,兼备了
性加密与公开密钥方法结合起来,兼备了 者的优点。
者的优点。
If something geos Very Wrong Way (tm), don't panic. Any way you still have unencrypted partition to boot from.
如果出了什麽错误,不要紧张。你始终可以从非加密的分区启动。
That it is using secure, encrypted network connectivity tools instead of telnet, ftp, rlogin, rsh and rcp tools.
它用安全、加密的网络连接工具代替了 telnet、ftp、 rlogin、rsh 和 rcp 工具。
In SNA products, a key used to encipher operational keys that are to is used at a node.
在系统网络体系结构(sna)产品中,对将要在某个网点上使用的操作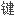 标进行加密的一种
标进行加密的一种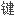 (
(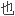
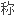
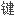 标,
标,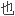 就是密钥)。
就是密钥)。
Using the program to generate 3-D multi-block abutting structured grid of reverse jet flow field with the controlling of concentration and orthogonalization.
并在此基础上采用一定的加密、正交化方法,生成了三维反向喷流流场分区对接结构网格。
RFID has the feature against reproduction, combined encryption, and securer data on ticket, document, certificate, and items, for the purpose of anti-counterfeiting.
RFID具有不可复制,多重加密,数据更加安全的特点,用于票据、证件、物品上,达到防伪目的。
Image array disturbed algorithm has been improved to implement multiple permute better.The algorithm shortens its encryption time, so it fits image encryption well.
为了更好的实现多步置乱,对图像位置置乱算法进行了改进,改进后的算法提升了混沌位置置乱加密速度,符合图像加密的需要。
The text discusses computer's principle and method of special information encipher and decipher. The text indicates program example of encipher and decipher and its actual application.
分析在计算机信息安全工作中,在大量信息共享的基础上,选择特定重要的信息,进行加密和解密的可逆方法.举出简单的加密程序和解密程序,最后探讨了加密应用操作的技巧.
In this paper, the authors described the decimal system encryption based on AES and its implementation in detail, and discussed a kind of encryption principle suitable for trustless channel.
详细描述了基于AES的十进制加密算法的实现过程和一种适合于不可靠信道(预付费系统与终端之间的通信实现非接触无介质代码传送)的加密算法实现原理。
In this scheme we put forward the concept of matrix pool on which our key predistribution scheme is upbuilt,and encrpytion scheme is introduced into the process of key transfer.
该方案提出了矩阵池的概念,将密钥的预配置建立在多个密钥矩阵之上,节省了节点的存储空间,增强了网络的可扩展性。将加密传输机制应用到密钥的传输过程中,增强了密钥传输过程中的安全性。
声明:以上例句、词性分类均由互联网资源自动生成,部分未经过人工审核,其表达内容亦不代表本软件的观点;若发现问题,欢迎向我们指正。
Luminary monolithic integrated circuit, LM3S series code encryption, introduction encipherment scheme.
Luminary单片机,LM3S系列代码加密,介绍加密方案。
Proposes pictureencryption algorithm based on the double unidimensional chaos system.
摘要 提出了一个基于双一维混沌系统的图像加密算法。
Gamic's fierce Indri guards carry Gamic, their High Priest, to the offering ceremony.
祭司加密科面目狰狞的亲卫队

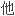 来主持更生仪式。
来主持更生仪式。
The security of encryption algorithms depends heavily on the computational infeasibility of brute force attack.
加密算法的安全性很大程度上取决于暴力破解的不可行性。
CSP layer provides briefness and wieldy function library for trader doing encrypt integration.
CSP层,即抽象设备层,其为加密服务集成商提供的简单、易用接口函数库。
Hadorwould traditionary symmetry encryption and publicity secret key mode band together, have two both the virtue.
将传统的对称性加密与公开密钥方法结合起来,兼备了 者的优点。
者的优点。
If something geos Very Wrong Way (tm), don't panic. Any way you still have unencrypted partition to boot from.
如果出了什麽错误,不要紧张。你始终可以从非加密的分区启动。
That it is using secure, encrypted network connectivity tools instead of telnet, ftp, rlogin, rsh and rcp tools.
它用安全、加密的网络连接工具代替了 telnet、ftp、 rlogin、rsh 和 rcp 工具。
In SNA products, a key used to encipher operational keys that are to is used at a node.
在系统网络体系结构(sna)产品中,对将要在某个网点上使用的操作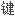 标进行加密的一
标进行加密的一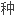
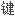 (
(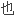 称
称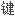 标,
标,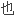 就是密钥)。
就是密钥)。
Using the program to generate 3-D multi-block abutting structured grid of reverse jet flow field with the controlling of concentration and orthogonalization.
并在此基础上采用一定的加密、正交化方法,生成了三维反向喷流流场分区对接结构网格。
RFID has the feature against reproduction, combined encryption, and securer data on ticket, document, certificate, and items, for the purpose of anti-counterfeiting.
RFID具有不可复制,多重加密,数据更加安全的特点,用于票据、证件、物品上,达到防伪目的。
Image array disturbed algorithm has been improved to implement multiple permute better.The algorithm shortens its encryption time, so it fits image encryption well.
为了更好的实现多步置乱,对图像位置置乱算法进行了改进,改进后的算法提升了混沌位置置乱加密速度,符合图像加密的需要。
The text discusses computer's principle and method of special information encipher and decipher. The text indicates program example of encipher and decipher and its actual application.
分析在计算机信息安全工作中,在大量信息共享的基础上,选择特定重要的信息,进行加密和解密的可逆方法.举出简单的加密程序和解密程序,最后探讨了加密应用操作的技巧.
In this paper, the authors described the decimal system encryption based on AES and its implementation in detail, and discussed a kind of encryption principle suitable for trustless channel.
详细描述了基于AES的十进制加密算法的实现过程和一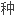 适合于不可靠信道(预付费系统与终端之间的通信实现非接触无介质代码传送)的加密算法实现原理。
适合于不可靠信道(预付费系统与终端之间的通信实现非接触无介质代码传送)的加密算法实现原理。
In this scheme we put forward the concept of matrix pool on which our key predistribution scheme is upbuilt,and encrpytion scheme is introduced into the process of key transfer.
该方案提出了矩阵池的概念,将密钥的预配置建立在多个密钥矩阵之上,节省了节点的存储空间,增强了网络的可扩展性。将加密传输机制应用到密钥的传输过程中,增强了密钥传输过程中的安全性。
声明:以上例句、词性分类均由互联网资源自动生成,部分未经过人工审核,其表达内容亦不代表本软件的观点;若发现问题,欢迎向我们指正。
Luminary monolithic integrated circuit, LM3S series code encryption, introduction encipherment scheme.
Luminary单片机,LM3S系列代码加 ,介绍加
,介绍加 方案。
方案。
Proposes pictureencryption algorithm based on the double unidimensional chaos system.
摘要 提出了一个基于双一维混沌系统的图像加 算法。
算法。
Gamic's fierce Indri guards carry Gamic, their High Priest, to the offering ceremony.
祭司加
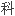

 狰狞的亲卫队抬着他来主持更生仪式。
狰狞的亲卫队抬着他来主持更生仪式。
The security of encryption algorithms depends heavily on the computational infeasibility of brute force attack.
加 算法的安全性很大程度上取决于暴力破解的不可行性。
算法的安全性很大程度上取决于暴力破解的不可行性。
CSP layer provides briefness and wieldy function library for trader doing encrypt integration.
CSP层,即抽象设备层,其为加 服务集成商提供的简单、易用接口函数库。
服务集成商提供的简单、易用接口函数库。
Hadorwould traditionary symmetry encryption and publicity secret key mode band together, have two both the virtue.
将传统的对称性加 与公开
与公开
 方法结合起来,兼备了
方法结合起来,兼备了 者的优点。
者的优点。
If something geos Very Wrong Way (tm), don't panic. Any way you still have unencrypted partition to boot from.
如果出了什麽错误,不要紧张。你始终可以从非加 的分区启动。
的分区启动。
That it is using secure, encrypted network connectivity tools instead of telnet, ftp, rlogin, rsh and rcp tools.
它用安全、加 的网络连接工具代替了 telnet、ftp、 rlogin、rsh 和 rcp 工具。
的网络连接工具代替了 telnet、ftp、 rlogin、rsh 和 rcp 工具。
In SNA products, a key used to encipher operational keys that are to is used at a node.
在系统网络体系结构(sna)产品中,对将要在某个网点上使用的操作键标进行加 的一种键(也称键标,也就是
的一种键(也称键标,也就是
 )。
)。
Using the program to generate 3-D multi-block abutting structured grid of reverse jet flow field with the controlling of concentration and orthogonalization.
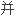 在此基础上采用一定的加
在此基础上采用一定的加 、正交化方法,生成了三维反向喷流流场分区对接结构网格。
、正交化方法,生成了三维反向喷流流场分区对接结构网格。
RFID has the feature against reproduction, combined encryption, and securer data on ticket, document, certificate, and items, for the purpose of anti-counterfeiting.
RFID具有不可复制,多重加 ,数据更加安全的特点,用于票据、证件、物品上,达到防伪
,数据更加安全的特点,用于票据、证件、物品上,达到防伪 的。
的。
Image array disturbed algorithm has been improved to implement multiple permute better.The algorithm shortens its encryption time, so it fits image encryption well.
为了更好的实现多步置乱,对图像位置置乱算法进行了改进,改进后的算法提升了混沌位置置乱加 速度,符合图像加
速度,符合图像加 的需要。
的需要。
The text discusses computer's principle and method of special information encipher and decipher. The text indicates program example of encipher and decipher and its actual application.
分析在计算机信息安全工作中,在大量信息共享的基础上,选择特定重要的信息,进行加 和解
和解 的可逆方法.举出简单的加
的可逆方法.举出简单的加 程序和解
程序和解 程序,最后探讨了加
程序,最后探讨了加 应用操作的技巧.
应用操作的技巧.
In this paper, the authors described the decimal system encryption based on AES and its implementation in detail, and discussed a kind of encryption principle suitable for trustless channel.
详细描述了基于AES的十进制加 算法的实现过程和一种适合于不可靠信道(预付费系统与终端之间的通信实现非接触无介质代码传送)的加
算法的实现过程和一种适合于不可靠信道(预付费系统与终端之间的通信实现非接触无介质代码传送)的加 算法实现原理。
算法实现原理。
In this scheme we put forward the concept of matrix pool on which our key predistribution scheme is upbuilt,and encrpytion scheme is introduced into the process of key transfer.
该方案提出了矩阵池的概念,将
 的预配置建立在多个
的预配置建立在多个
 矩阵之上,节省了节点的存储空间,增强了网络的可扩展性。将加
矩阵之上,节省了节点的存储空间,增强了网络的可扩展性。将加 传输机制应用到
传输机制应用到
 的传输过程中,增强了
的传输过程中,增强了
 传输过程中的安全性。
传输过程中的安全性。
声明:以上例句、词性分类均由互联网资源自动生成,部分未经过人工审核,其表达内容亦不代表本软件的观点;若发现问题,欢迎向我们指正。